No one wants cyber criminals making off with confidential customer information or trade secrets. And companies cannot afford the downtime associated with a denial of service. Given that compromised data can lead to the downfall of a business, it’s not surprising that IT leaders are concerned about the security of cloud platforms.
So when looking for an IT infrastructure monitoring tool, some IT leaders hesitate to move forward with a cloud-based solution. While putting on the brakes before subscribing to a cloud monitoring solution is understandable and can give time for proper vetting of vendors, completely opting out comes at a high cost. That’s because as companies migrate more of their technology to the cloud, only a SaaS solution can give them a bird’s-eye view of their entire IT infrastructure. And that’s what they need to manage it efficiently and successfully.
Given that, what should you look for to determine that your IT infrastructure monitoring tool will keep your data safe?
A cloud monitoring solution is safe if:
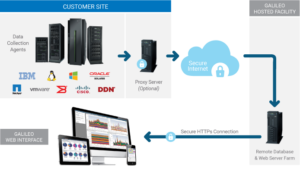
An Agent Collects Data on Location
An agent should collect performance metrics wherever your data is located, whether it’s at a cloud provider or in an on-site data center.
The Agent Is Registered and Authenticated
Your supplier should register and authenticate the on-site agent using a Certificate Authority. This process:
- Establishes an encrypted link to keep the data private and secure in the cloud, ensuring it cannot be intercepted en route to the vendor of your SaaS infrastructure monitoring tool
- Acts as a passport for your data, allowing it through the gate while keeping out data from unauthorized agents
It Operates on a One-Way Street
You should send the data out, but there’s no need to receive data back that could cause havoc on-site.
It Only Collects Performance Metrics
No healthcare facility is allowed to distribute private patient information, no bank can share Personally Identifiable Information (PII), and no high-tech company can afford to give out new product development secrets. In fact, most businesses want to minimize the data that goes outside their IT infrastructure.
The good news is, there is no need for your cloud infrastructure monitoring tool to have access to your databases and other company information. It should only collect performance metrics.
It Protects Server Information
While some companies are comfortable allowing an agent to collect server information, such as IP addresses, hostnames, server models and serial numbers, others are not. If you’re inclined to keep this identifying information in your safety vaults, look for a vendor that offers the option of either scrambling it or removing this data before transmission.
It Locates Data in a Secured Colocation Space
Even though your SaaS monitoring tool vendor should only collect performance data, financial institutions and others still want to keep it secure. Make sure your vendor has their data center in a secured colocation space that is accredited by the Statement on Standards for Attestation Engagements 16 (SSAE 16) as set forth by the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA). Also look for accreditation by the Service Organization 2 (SOC 2) Type II.
It Offers a Secure Web Portal
You’ll need a web portal to view dashboards that depict the vital stats on your IT infrastructure’s performance, capacity, and configuration. You should be able to view it over an HTTPS connection that a trusted third-party Certificate Authority has certified. Of course, it must also be password protected, providing access to authorized users only.
It’s Physically Secure
You don’t want your data to be at risk of assaults by people or natural disasters. So make sure your vendor:
- Uses a facility that is not likely to be compromised or destroyed by a hurricane, flood or another weather-related calamity
- Provides a data center that is secured from human intervention, for instance by having no identifiable signage outside and using biometric scanning for access
- Operates cameras around the clock that monitor security
- Uses power and cooling systems that are behind gated fences
The Vendor Follows Sound Security Policies
If a SaaS vendor is concerned about security, they will have a set of standard security policies. These should cover areas such as access control, antivirus protection, computer security, employee background checks and more.
To feel safe in the cloud, vet your vendor to ensure they have a multifaceted approach to security that rules out data breaches, network intrusion or a denial of service.